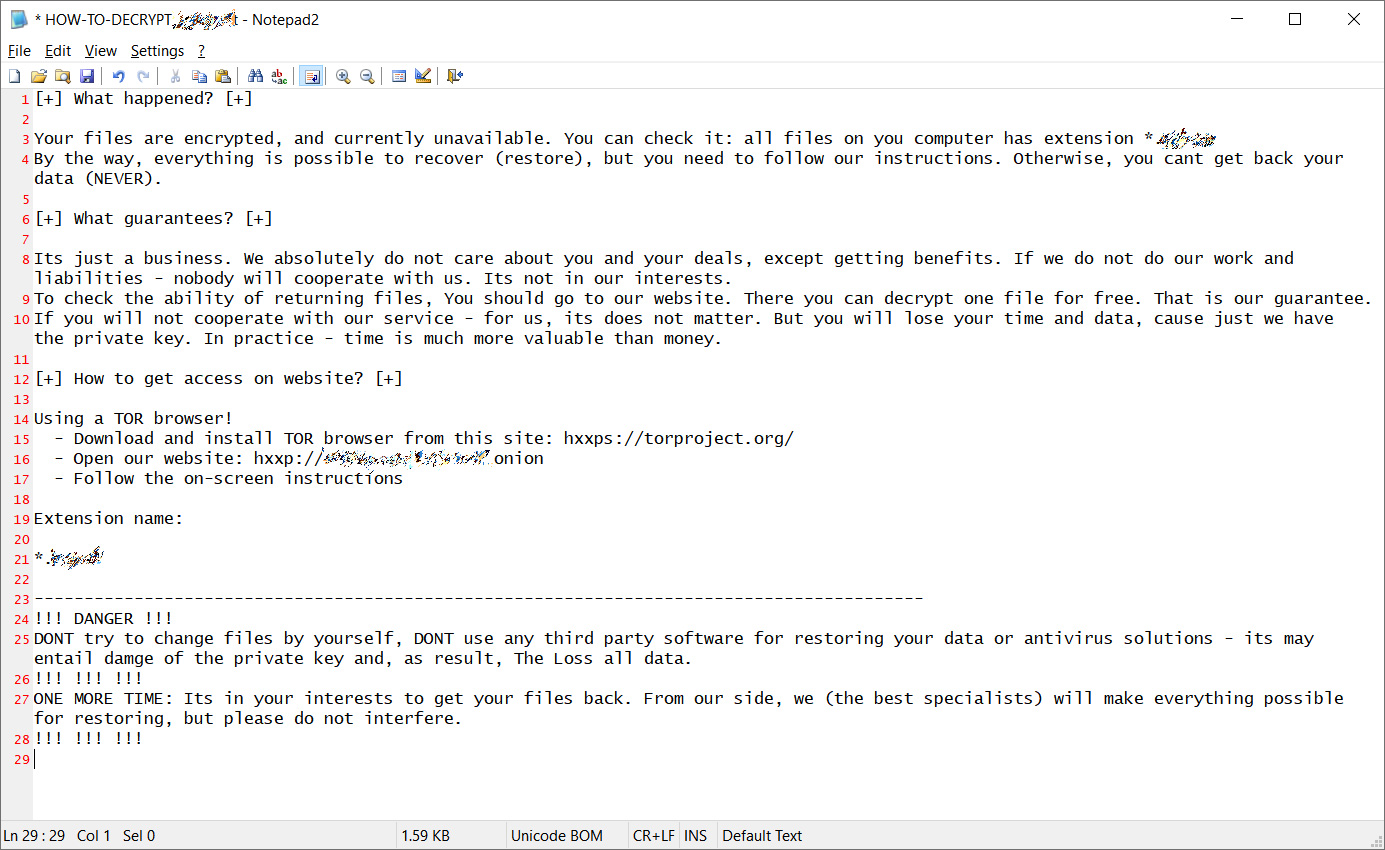
The tremendous success of ransomware infections over the past year showed cybercriminals that holding data for ransom is the key to making money from online attacks. Ransom-based attacks are evolving, and if enterprise defenders aren’t careful, they are going to soon see more ransom notes popping up on their servers, databases, and back-end applications.
Consider last week’s events: After Victor Gevers, a security researcher and founder of GDI Foundation, reported several hundred instances of publicly exposed MongoDB installations had been wiped and held for ransom over the previous two weeks, several other attackers joined in, bumping the number of compromised databases from several hundred to more than 10,000.
The attackers didn’t need to bother with malware to gain access to the database or the information saved within—the door was wide open since these MongoDB installations used the default configuration, which allowed unauthenticated connections via port 27017. These databases were fully accessible from the internet, and anyone connecting via that port had full administrator rights to read, create, update, and delete records.
While compromising a few systems and encrypting the data in large enterprises will continue to be lucrative—healthcare facilities paid out thousands of dollars in 2016 to regain control of their data and systems—attackers are going to change tactics to keep their income stream flowing. Databases, web servers, application servers, enterprise resource planning (ERP) systems, and other enterprise applications all contain valuable information that can disrupt business operations if stolen.
“Attackers are always looking to increase the value of what they steal,” said Jeff Schilling, chief of operations and security at cloud security provider Armor.
It’s a safe bet that even if the enterprise doesn’t use MongoDB, which is widely used in big data and heavy analytics environments, it may be running other servers or applications that are accessible from the internet and vulnerable to attack. Criminals can easily shift their attacks to those servers and applications. Already, last spring, researchers from Cisco’s Talos Security Intelligence and Research Group found that attackers were exploiting vulnerabilities in JBoss application servers to spread SamSam ransomware.
New targets, new victims
The data contained on those systems don’t have to be something the attacker can sell on the black market—it just needs to be valuable to the owner. It doesn’t matter if the database or back-end system doesn’t have financial data or transactional information. Application source code, personnel files, organization data, and entire application servers are all valuable.
“As long as it’s valuable to someone, attackers can target it for ransomware in order to make a profit,” said Jordan Wright, an R&D engineer at authentication company Duo Security.
Ransoms are most effective when there are no backups to restore the data. While most enterprises typically have some kind of backup strategy in place for databases and critical enterprise applications, they may still be forced to pay because of the perception that it will take too long to restore from backups.
In the case of those enterprises with compromised MongoDB installations, at least 20 victims sent the 0.2 BTC ransom (about $220 at current prices) to the BitCoin address used by the initial attacker between Dec. 21, 2016 and Jan. 6, 2017, according to information available on Blockchain.info.
Imagine being an Oracle or SAP administrator and one day finding that an attacker had copied all the data and then wiped the systems.
In case the idea of data stolen from code repositories and databases wasn’t scary enough, software-as-a-service applications could become the next ransom target, Schilling said. An attacker could demand the ransom from the SaaS provider by successfully breaking into the network and disrupting operations, or from the SaaS customer by preventing the customer from accessing the data. A network breach on the provider side seems unlikely, but not impossible, since SaaS companies tend to invest heavily in securing their infrastructure.
But then, the massive DDoS attack against DNS provider Dyn affected SaaS providers adversely, without even touching their networks. That ransom demand could have gone sky-high, had the attackers gone that route.
Customer-side ransoms sound even more likely. There are already ransomware strains capable of encrypting data on cloud storage sites by infecting a computer that had a synced folder. Attackers can use stolen or compromised credentials to gain access to the customer’s SaaS instance and all the associated data. Whether the customer would pay would depend on how quickly—and completely—the provider would be able to restore the data.
All kinds of attacks, not just malware
It will be a mistake to keep focusing on the malware. Yes, there are reports of ransomware on Smart TVs, and malware will continue to encrypt data stored in enterprise networks. However, ransomware isn’t the only way cybercriminals have extorted enterprises in the past, and it isn’t going to be the only approach going forward.
Remember that the attackers behind Sony Pictures demanded “monetary compensation.” And ProtonMail and Feedly both were slammed with distributed denial-of-service attacks when they refused to pay.
Cybercriminals are going to make money however they can, and if it is easier to compromise the database by exploiting unpatched remote code execution vulnerabilities and escalation of privilege flaws, or through spear phishing, they aren’t going to bother to try to infect the server with malware. Or they may use a combination of scripting languages such as PowerShell and JavaScript to compromise systems, which doesn’t leave behind any malware samples for defenders to detect.
Defender checklist
Attackers are trying to figure out which types of data companies consider valuable, and which organizations are more likely to pay. The initial MongoDB attacks were originally nondiscriminating and compromised any open MongoDB installations, but security researchers believe the latest attacks are more selective, targeting healthcare providers, telecommunications companies, data brokers, and electric utility firms.
IT teams need to expand their focus and look at all the various ways their data could be stolen. Don’t get bogged down looking for malware samples or signs of infections, because the attacker demanding the ransom may use other methods to hold the data.
Attackers connected to vulnerable MongoDB installations via port 27017. Organizations using the default installation of MongoDB should update their software, set up authentication, and lock down port 27017.
That advice applies to other databases, servers, and applications as well. ERP systems such as SAP need to be configured to consider security. Database ports should be locked down. Software updates should be applied as soon as possible. Restrict remote access and require strong authentication for any user accounts that require remote access rights.
Administrators need to control and limit access to their organization’s data stored in their servers as well as in cloud applications. “Without mitigating controls like two-factor authentication, attackers can take over the data a user has access to by simply sending a phishing email,” Wright said.
IT teams need to stop thinking of ransomware as a malware infection and start thinking of a broad range of attacks that have an extortion component. This means beefing up data breach detection capabilities, securing systems so that data can’t be easily obtained, protecting the data even when defenses fail, and improving incident analysis so they can investigate thoroughly when something goes wrong. The attacks against MongoDB installations are just the beginning.
http://www.infoworld.com/article/3155435/cyber-crime/mongodb-ransomware-attacks-sign-criminals-are-going-after-servers-applications.html