Virtual Desktop Infrastructure (VDI) adding security to your organization
/in Cloud, Collaboration, Computer Technology, Cyber-security, Network Infrastructure, Network Security, Work from home /by Carl EasterdayVirtual desktop infrastructure (VDI) has many benefits (among them):
- A scalable infrastructure: Virtual desktops have become more appealing due to the cloud. By using adaptable infrastructure to provide resources as needed, the consolidation of the full VDI desktop infrastructure onto a host server lowers overall costs because businesses don’t have to purchase or maintain the necessary hardware.
- Management structure: The virtual desktop infrastructure allows administrators to patch, maintain, and modify all virtualized desktops simultaneously. As a result, there is no need to repair and maintain the entire network of desktop computers on an individual basis. Moreover, in the event of a major disruption, the data center has all information backed up and supported.
- Enhanced Security: VDI desktop services allow organizations to preserve and protect their sensitive information because the data isn’t stored on the users’ individual devices but within the data center. If the employee’s laptop, desktop, or other device is compromised, the hacker cannot access the organization’s data. Of course, the effectiveness of the security will depend upon the IT team’s vigilance regarding system management, and the authentication process for the remote users has to be rigid and scrupulously maintained.
- Improved user experience. Employees are allowed to use the device of their choice in the manner of their choice, making the remote working experience easier and more convenient.
- Lower cost. The overheads for maintaining legacy hardware will be lowered considerably due to the reduced need to upgrade and maintain in-office hardware.
Our team, in conjunction with our skilled engineers at GCSIT, can help your organization plan, procure, implement and support your VDI solution.
How to Secure your Off-Site Veeam Backups
/in Cyber-security, Data, Network Infrastructure, Network Security /by Carl EasterdayMicrosoft NCE (New Commerce Experience) and how it will impact your organization
/in Cloud, Collaboration, News, Work from home /by Carl EasterdayMicrosoft is releasing the details of the Microsoft NCE (New Commerce Experience) on January 10th, 2022.
This is a price increase for Microsoft 365 and a change in the commitment process.
– January 10, 2022: Microsoft will launch the general availability of NCE for Modern Work and Dynamics 365 for indirect partners to offer to CSP re-sellers. Microsoft will also offer two time-bound promotions to incentivize users via their reseller partners, to migrate to NCE.
These promos are:
5% off annual subscriptions January through March 2022
Monthly subscriptions will be available at annual pricing from January through June 2022.
So, this would require you to sign up with your reseller and change from a month-to-month contract to an annual contract. There is an option to stay month-to-month, but there is a 20% premium fee!
– March 1, 2022: There will be a price increase for the following products:
Enterprise:
Office 365 E1: $10 (from $8)
Office 365 E3: $23 (from $20)
Office 365 E5: $38 (from $35)
Microsoft 365 E3: $36 (from $32)
SMB:
Microsoft 365 Business Basic: $6 (from $5)
Microsoft 365 Business Premium: $22 (from$20).
Please note Microsoft is NOT changing pricing for Microsoft 365 E5, Microsoft Business Standard, or the Frontline SKUs.
– March 10, 2022: All new subscriptions for Modern Work and Dynamics will be required to be procured through the NCE Platform.
– July 1, 2022: All renewal subscriptions for Modern Work and Dynamics will be required to be procured through NCE Platform. Pax8 will no longer allow partners to renew customer subscriptions on CSP legacy.
– October 1, 2022: Incentives only available for NCE transactions (through MCI).
– July 2023: All non-migrated client subscriptions must be moved to the New Commerce Experience.
What Does This Mean for You?
Moving to the New Commerce Experience will help you prepare for future growth thanks to improved revenue predictability, reduced licensing complexity, multiple term options, and features that enable new sales capabilities and operational efficiencies. You can expect:
Term Options
– Monthly term options at 20% premium – if you want to stay on month-to-month, there is a 20% premium in cost.
– Annual term options; upfront or monthly payments
– Tri-annual term options; upfront, annual, or monthly payments
– Cancelation period is now 3 days, including day of purchase. There will be a full refund issued if canceled on day 1, and a pro-rated refund if cancelled on days 2 and 3.
Windows 365: Windows 365 subscriptions will only be available via the monthly term offer on NCE. Windows 365 subscriptions will not be subject to the 20% premium for monthly terms at this time.
Nonprofit and Education: Nonprofit and Education licenses will not be offered on NCE at this time. Non- Profit and Education products will not be affected by the price increases in March.
Cyber-Security Insurance and Requirements
/in Uncategorized /by Carl EasterdayCybersecurity insurance requirements
Cisco drives that operate for 40k hours will cease to function
/in Cisco, Data, News /by Carl EasterdayCisco just announced a new Field notice regarding Defect ID CSCvt55829 which is an industry wide firmware index bug.
Under normal operation, after 40,000 power-on hours (4.5 years), the SSD will report that 0 GB of available storage space remains. The drive will go offline and become unusable.
These drives were used in the following C-Series products and there is a firmware upgrade to resolve the issue. For more information you can go to the Field Notice FN – 70545.
| UCS Manager based B and C-Series Software Release | Software Downloads |
|---|---|
| Release 4.1(1c) and later |
VMware code execution flaw CVE-2021-21972
/in Cyber-security, Network Infrastructure, Network Security, News, Uncategorized /by Carl EasterdayThere is a newly disclosed code-execution vulnerability in VMware vCenter. VMware was quick to release a patch (within a day) and it can be found here.
The severity of this vulnerability as well as the fact that there are exploits available for both Windows and Linux servers, kicked off a flurry of mass scanning for vulnerable vCenter Servers.
Code execution, no authorization required
CVE-2021-21972 allows hacker with no authorization to upload files to vulnerable vCenter servers that are publicly accessible over port 443, researchers from security firm Tenable said. Successful exploits will result in hackers gaining unfettered remote code-execution privileges in the underlying operating system. The vulnerability stems from a lack of authentication in the vRealize Operations plugin, which is installed by default.
The flaw has received a severity score of 9.8 out of 10.0 on the Common Vulnerability Scoring System Version 3.0. Mikhail Klyuchnikov, the Positive Technologies researcher who discovered the vulnerability and privately reported it to VMware, compared the risk posed by CVE-2021-21972 to that of CVE-2019-19781, a critical vulnerability in the Citrix Application Delivery Controller
Ransomware and the impact to your business
/in Cyber-security, Network Security, News /by Carl EasterdayEveryday, you read another story about how a company has been hit by a ransomware attack, which potentially can disrupt your business, services to your clients and livelihood of your employees.
Just last week it was announced another company, Forward Air, was hit by a ransomware attack, which disrupted services and impacted revenue. This attack was attributed to a group “Hades”. Forward Air, a trucking company from Tennessee, posted revenues of $1.4 billion in 2019 and employs more than 4300.
The ransomware note, resembles a similar note used by another ransomware group known as “REvil”, also known as “Sodin”.
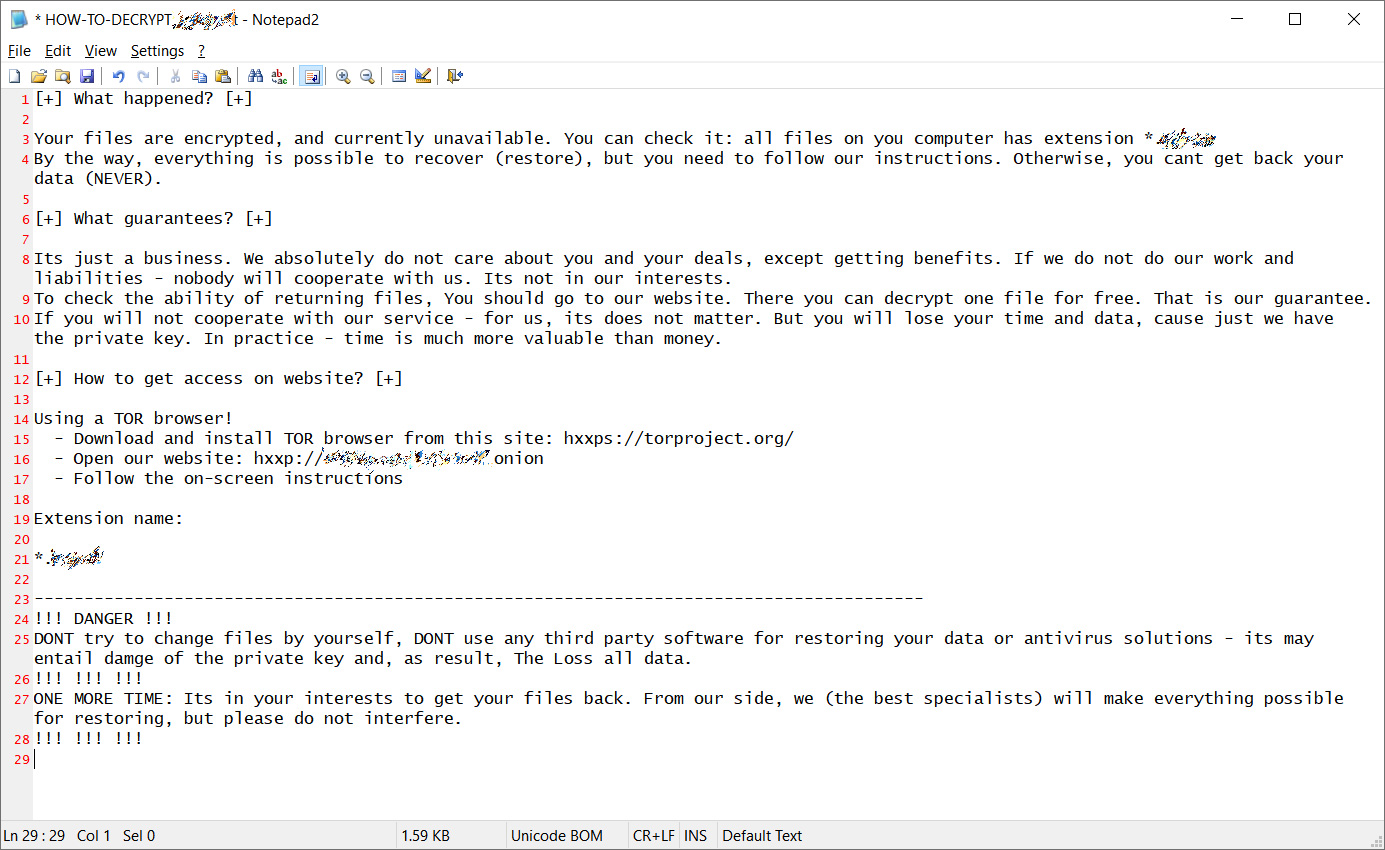
This is a Sodinokibi variant that was first seen in early 2019. Sodinokibi is what is known as ransomware-as-a-service, basically a software package which is catered by underground vendors to threat actors providing them a ransomware platform tool.
Companies are limited in their ability to defend against this type of exploitation, especially if they do not have full time IT staff or contracted Managed Service Providers that focus on security. Your organization must follow the following guidelines to help mitigate your exposure:
- Patch aggressively so vulnerabilities are eliminated and access routes are contained
- Enable endpoints with tools that automatically detect and respond to infections before they become systemwide
- Enable network threat intelligence tools to detect anomalies in your network traffic
- Make sure emails are screened for malicious payloads and links
- Minimize access levels by employees to perform their job functions
If you have been hit by ransomware, or just want to assess your company’s state of preparedness, reach out to us to discuss your needs.
LMJ is a full service Managed Service Provider, with offices in Alaska and California.