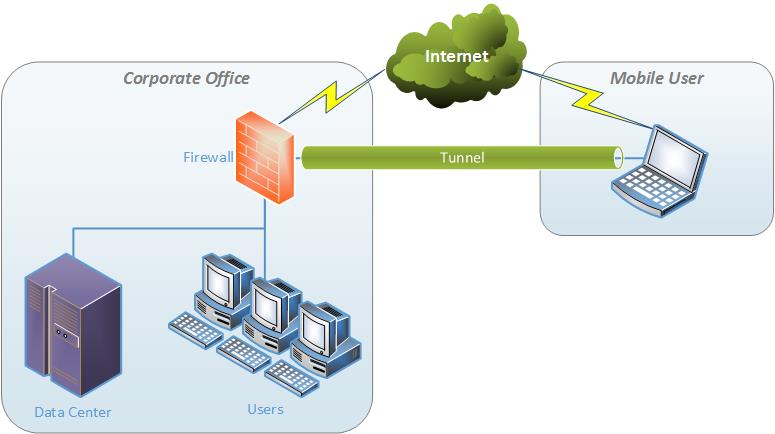
A VPN (Virtual Private Network) is a means of securely connecting offices and remote users to the corporate network over the public Internet. They provide a cost effective means of replacing expensive private circuits and are the foundation for mobile workforce integration. To learn more about how they function, read on.
Types of VPNs
There are essentially two types of VPNs; Site-to-Site and Remote Access.
Site-to-Site VPNs
Site-to-Site VPNs connect branch offices to the corporate network and are transparent to the users. Most commonly, Site-to-Site VPNs use IPsec protocols to establish a secure tunnel between the sites.

Remote Access VPNs
Remote Access VPNs allow individual users to connect to the corporate network from anywhere there is an Internet connection.
Security
To ensure the privacy of data as it transits the public Internet, authentication and secure protocols must be used.
Authentication, Encapsulation, and Encryption
Authentication prevents unauthorized users from accessing the VPN. Encapsulation wraps the private data with a header that allows it to traverse the public network. Encryption protects the privacy of the data being sent. Site-to-Site VPNs typically use IPSec protocols to secure the connection.
Site-to-Site VPNs (IPsec)
IKE (Internet Key Exchange) defines a mechanism to secure the data transmission between two IPSec peers. IKE uses ISAKMP (Internet Security Association and Key Management Protocol) for key-exchange. The key-exchange takes place in two phases.
Phase 1 (Authentication)
Phase 1 is the authentication phase and establishes a secure communication channel. Two modes are available; Main Mode and Aggressive Mode.
Main Mode
Main Mode uses six messages to negotiate the security policy that will protect the phase 2 messages, perform a Diffie-Hellman key exchange and pass nonces (random numbers used for signing), and lastly peer authentication.
There are four methods to authenticate IPSec peers:
Pre-Shared Keys (PSK) is a shared secret distributed out of band to the peers. The peers use the PSK and nonces to create a hash that is used to authenticate messages.
Digital Signatures (RSA or DSS) uses digital certificates of the peers exchanged in the last two messages to calculate the hashes used to authenticate the peers.
RSA Public Key Encryption requires both peers to have a public-private key-pair that they use to encrypt/decrypt messages. Nonces exchanged are secured through this process and are used to create the hashes to authenticate each other.
Revised RSA Public Key Encryption is similar to the prior method but reduces the number of public key operations from four to two and, instead, uses two symmetric-key operations.
Aggressive Mode
Aggressive Mode only requires three messages to establish the IKE SA. However, the identities of the parties are revealed. Aggressive mode is used in cases where the branch office’s Internet connection has a dynamic IP address.
Phase 2 (Key Exchange)
Also called “Quick Mode”, it is used to establish the IPsec SA and to generate new keying material. A full Diffie-Hellman key exchange can be executed to provide perfect forward security (PFS).
Remote Access VPNs
Remote access VPNs can use a variety of secure protocols including IPSec (explained above in Site-to-Site VPNs), SSL/TLS, DTLS, and SSTP.
SSL/TLS
SSL (Secure Sockets Layer) allow a VPN to be established from a web browser. This has the advantage of ease of use over IPSec remote access VPNs that must use client software. It will also work in environments where IPsec may be blocked at the network edge but there are issues tunneling over UDP.
DTLS
DTLS (Dynamic Transport Layer Security) solves the SSL/TLS UDP tunneling issues and is used by Cisco AnyConnect and OpenConnect VPN.
SSTP
SSTP (Secure Socket Tunneling Protocol) was introduced with Microsoft Windows Server 2008 and tunnels PPP (Point-to-Point Protocol) or L2TP (Layer 2 Tunneling Protocol) through an SSL 3.0 channel.
Tunneling
Tunneling is a method of transferring data from one network to another over an intermediate network infrastructure.
The data (payload) to be transferred is encapsulated in a frame with an additional header that provides the routing information so the encapsulated payload can traverse the intermediate network. The logical path through the intermediate network is called a tunnel. The term “tunneling” refers to the entire process of encapsulation, transmission, and de-encapsulation at the destination. Examples of tunneling protocols include PPTP (Point-to-Point Tunneling Protocol), and L2TP (Layer 2 Tunneling Protocol).
Routing
Routing from a VPN endpoint can either be Default (Tunnel All) or Split Tunnel.
Default (Tunnel All)
With Default routing, all traffic from the source is tunneled to the destination network. Traffic for the destination network and Internet bound traffic are both sent through the tunnel. The default route is through the tunnel.
Split Tunnel
Split Tunnel routing sends only the internal destination network traffic through the tunnel. Internet bound traffic is sent directly out the local Internet connection. The default route is to the Internet gateway.
Conclusion
VPNs are a secure and cost effective way to connect remote sites and mobile users by establishing private connections over the public Internet.