Mobile device usage has exploded on the IT scene and generated unprecedented demand for wireless network services. SmartPhones and Tablets are the majority of devices, but laptops continue to be extensively used as well. Adding to this wave of demand are the myriad of sensors being deployed in network aware devices and appliances that Cisco refers to as “The Internet of Everything”.
A business wireless network must provide secure connectivity normally for multiple classes of users (corporate and guest), coverage throughout the target service area, support for a wide variety of devices, and bandwidth for the desired applications.
Wireless Device Overview
Although extremely small offices of less than 10 people may be able to function with a consumer grade wireless network, most businesses will want the increased security and service levels provided by business grade components. Wireless routers are common in residential wireless installations but are not a component of a business class wireless network. The components of a business class wireless network include the following.
Clients
Clients are the endpoint devices accessing the wireless network and can include laptops, SmartPhones, tablets, barcode scanners, environmental control systems, security cameras, and VoIP phones.
Wireless Access Points
Wireless Access Points (WAPs) are the actual devices that communication with clients wirelessly. They contain one or more radios and connect to the wired network to provide network connectivity. WAPs come in various models for indoor or outdoor use and with internal or external antennas depending on the desired application.

WAPs can operate in Autonomous mode or Lightweight mode. Autonomous WAPs are individually configured and managed and are appropriate for smaller installations of three or fewer WAPs. Lightweight WAPs rely upon a Wireless LAN Controller (WLC) for their configuration and management. For larger installations, use of one or more WLCs centralizes the configuration of WAPs enabling zero touch deployments throughout the enterprise.
WAPs require a power source to function. Although WAPs have a connector for an external power source, this is not very convenient given that most WAPS are installed some distance from a standard power outlet. Power over Ethernet (PoE) is a standard that delivers power over standard network cabling so that a WAP can be powered by the data cable used to connect it to the wired network. Power to this cable can be supplied by a PoE switch or the use of a power injector.

Controllers
Wireless LAN Controllers (WLCs) can be physical devices, virtual appliances, and even cloud hosted. The function of the WLC is to centrally manage the WAPs on the network, their configuration, the services they deliver, security, monitoring, alerting, and reporting. WLCs can operate with managed WAPs in either Tunnel mode or FlexConnect local switching mode. Each has advantages and disadvantages that make them the appropriate choice in different applications.

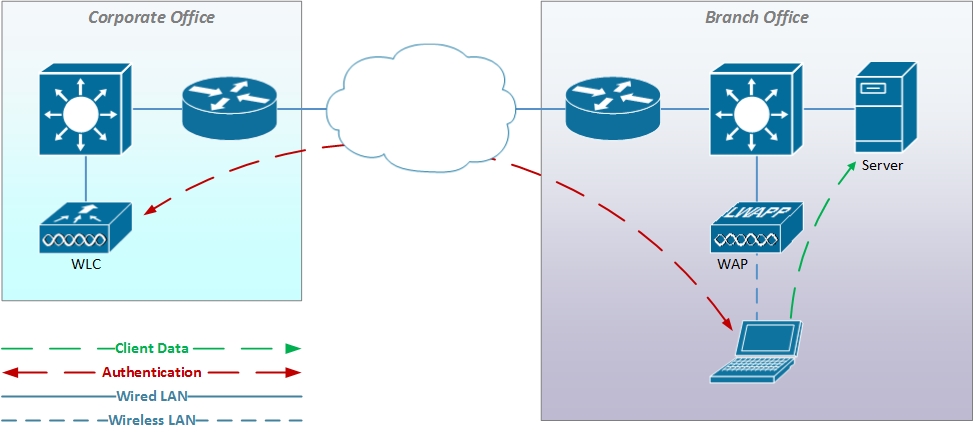
Tunnel Mode
In Tunnel mode operation, all traffic from the WAPs is delivered to the WLC via an encrypted tunnel. This includes both the session authentication traffic and the actual client traffic. The WLC decrypts the client traffic and drops it onto the LAN via the WLC’s network interface.
Tunnel mode has the advantage of secure transmission over the LAN and a potential for policy application at the WLC. However, if the WAP is located at a remote site and the WLC at the corporate office, all client traffic must transit the WAN link even if it is destined for hosts at the remote site. This can slow performance since the client traffic must transit the WAN link twice to reach local resources.
Since the WLC is in the middle of the entire traffic flow, operation in Tunnel mode is dependent on the WLC being available creating a potential point of failure.
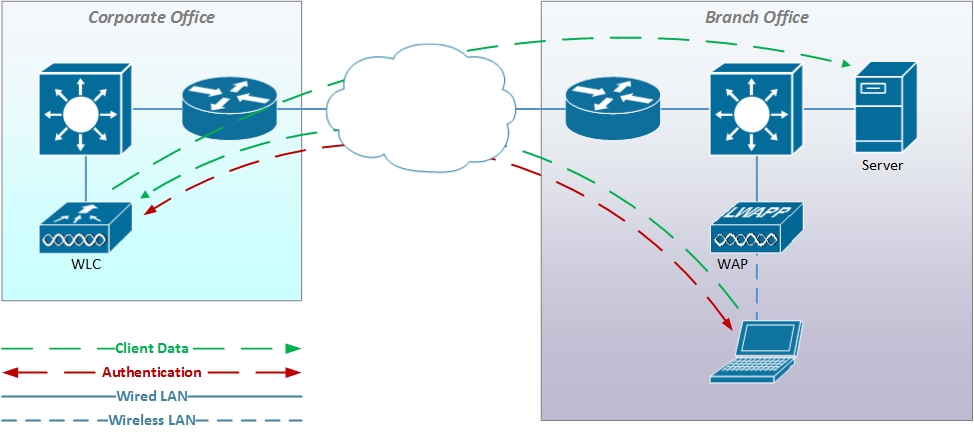
FlexConnect Mode
FlexConnect mode uses an encrypted tunnel to handle the client authentication request to the WLC. Once the client is authenticated the WAP is instructed to allow unencrypted client traffic onto the local switch that the AP is connected to. In the case of a WAP at a remote site and a WLC at the corporate office, this allows the client to directly access local resources without transiting the WAN connection (except to authenticate) which increases performance.
The WLC is required only to process the client authentication request. In FlexConnect mode, if the WLC goes offline any existing wireless client sessions will continue to function. However, new client sessions cannot be initiated until the WLC comes back online.
Wireless Protocols
There are numerous standards for wireless communications:
802.11a
The 802.11a standard was implemented in 1999 and operates in the 5 GHz band. The 5Ghz band is less crowded but has less range than the 2.4 GHz band and signals are more readily absorbed by walls and other objects. Maximum transmission speed is 54 Mbps.
802.11b
802.11b has a maximum transmission speed of 11 Mbps and operates in the 2.4 GHz band. It suffers from interference from other products that operate in the same frequency range including cordless phones, Bluetooth devices, and microwave ovens.
802.11g
In 2003, the 802.11g standard was ratified and, like 802.11b, operates in the 2.4 GHz band but with a maximum transmission speed of 54 Mbps. It suffers from the same interference issues as 802.11b.
802.11n
In 2009 the 802.11n proposed standard improved on the prior standards by adding multiple-input multiple-output (MIMO) antennas increasing the maximum throughput to 600 Mbps. This new performance threshold required that 802.11n WAPs be connected to Gigabit Ethernet switch ports. 802.11n is supported in both the 2.4 GHz and 5 GHz bands. The use of multiple antennas also enables additional functions such a beam forming (synchronization of transmissions from multiple antennas to amplify signals directed at clients further from the WAP).
802.11ac
802.11ac is a standard under development that will provide higher throughput (multi-station WLAN throughput of at least 1 Gbps and maximum single link throughput of at least 500 Mbps), more streams, and high-density modulation.
802.11ad
Also known as “WiGig” this published standard is seeing early adoption by hardware manufacturers. Using 60 GHz this new standard can deliver a theoretical maximum throughput of up to 7 Gbps and is expected to reach the market sometime in early 2014. It is important to note that this is a short-haul service that is intended to provide LAN connectivity. Because of the higher frequency the range will be shorter for a given transmission power level.
Channel Spacing in 2.4 GHz
The 2.4 GHz band is divided into 14 channels spaced 5 MHz apart. The availability of channels is regulated by country with North America using 1 through 11. Of these channels, only 1, 6, 11 are non-overlapping. Care must be taken to not use overlapping channels to avoid signal degradation and loss of throughput. Likewise, adjacent WAPs should use different channels to minimize interference a process that is automated in many controller based implementations.
Wireless Security
There are a wide variety of security measures available that vary widely in effectiveness.
Non-broadcast SSID
Not announcing the SSID is very easy to implement but offers virtually no protection except from the most unsophisticated attackers.
MAC Address Filtering
This method permits access only to devices known, pre-approved MAC addresses. However, an attacker can easily sniff the network to find the MAC address of an authorized user and spoof that MAC address to gain access.
Requiring Static IP Addresses
Typically a DHCP server provides dynamic IP addresses to clients. Requiring clients to be statically addressed makes it more difficult for the casual intruder but offers little protection from a sophisticated attacker. And, it can greatly inconvenience authorized users.
SSID Availability Scheduling
Wireless networks are typically operational 24×7 which offers a large attack surface to intruders. By scheduling the availability of wireless networks to be available only during required business hours the attack surface can be significantly reduced. The Meraki cloud managed wireless products offer this feature.
WEP
The Wired Equivalent Privacy (WEP) encryption standard was the original standard for wireless but serious flaws mean that it should never be used.
WPA
WiFi Protected Access (WPA) addresses the shortcomings of WEP and uses a Pre-Shared Key (PSK) of 8 to 63 characters. WPA can be cracked in as little as 12 minutes so WPA2 is to be preferred.
WPA2
WPA2 improves upon WPA by including the AES-CCMP algorithm as a mandatory feature.
RADIUS
RADIUS authentication can be used with WPA and WPA2 to require user authentication to enable a session. This has the added advantage that wireless access rights can be enabled or revoked on a user by user basis.
PEAP-MSCHAPv2
Protected Extensible Authentication Protocol (PEAP) was developed jointly by Cisco, Microsoft, and RSA Security as a means of security transport of data, passwords, and encryption keys with the need of a server. It can be combined with MSCHAPv2 for encrypted password authentication for wireless sessions and is one of the more common enterprise wireless security methods.
EAP-TLS
EAP-TLS uses digital certificates and a Public Key Infrastructure (PKI) to provide excellent security but with greater administrative overhead and complexity.
Two Factor Authentication
Smart cards, USB tokens, and software tokens can be used in combination with passwords to further secure wireless networks.
Deployment Planning
RF signal behavior is complex and unpredictable by nature. The typical business office is made up of many different types of materials each with a different RF opacity or reflectivity. Combine this with the variables introduced by users moving through the environment and furniture moves and the challenges become readily apparent.
Site Survey
A physical inspection of the office is necessary to determine the location and characteristics of construction materials and potential interference sources. For example, bathroom mirrors, stucco walls, stone slabs, and structural steel must be identified and located on a floor plan. An inventory of competing wireless networks must be taken.
Requirements Gathering
The following are some of the requirements that must be specified in order to properly plan a wireless deployment:
· Target coverage area
· SSIDs required (ie. Corporate and Guest)
· Network access allowed for each SSID
· Anticipated use of each SSID (important for bandwidth management)
· User density in each area within the coverage target (ie. conference rooms, meeting areas)
RF Simulation
Software that permits the modeling of the office space to test WAP placement is essential in the planning process. By tracing the floor plan of the building and appropriately specifying the RF characteristics of the environment, WAPs can be placed to provide both the signal coverage and user subscription levels desired.
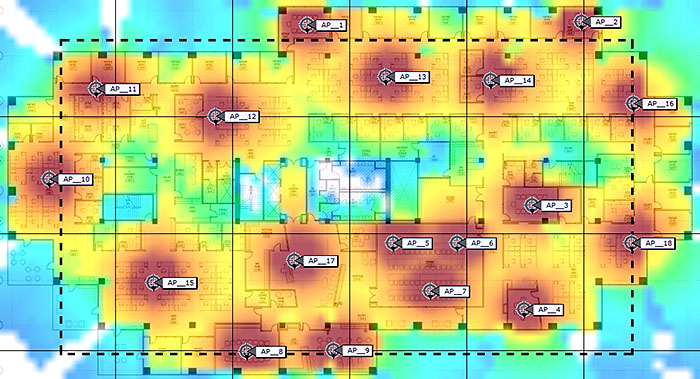
Generally speaking, 10-20 clients per radio per AP is a guideline that can be used for subscription levels. This can vary up or down based on the type of traffic generated by users. Planning WAP placement purely based on signal coverage often leads to performance issues from over-subscribed WAPs. It is frequently better to start by placing WAPs in high density areas like conference rooms to manage subscription levels and then evaluate the resulting simulation for coverage holes (weak signal coverage).
Advanced Settings
Controllers (and some WAPs) have the ability to steer clients to prefer the 5 GHz band where there is less interference. Some also have the ability to automatically load balance the subscription levels by pushing clients to adjacent WAPs. Controllers also have the ability to automatically adjust WAP channels and transmission power as conditions dictate and to detect and quarantine rogue WAPs.
Conclusion
Wireless networks are a business necessity as SmartPhones, tablets, and laptops become the predominant computing platforms. Fortunately, with recent advances in technology and security options, wireless networks have the potential to be secure and efficiently managed while delivering high value services to users.
Click here to add your own text
Click here to add your own text